Enable LDAP Server SSL
Why change?
Microsoft released a patch in mid-2020 that enforces LDAP Channel Binding and LDAP Signing.
/portal.msrc.microsoft.com//ADV190023
Any software that makes AD queries is affected.
support.microsoft.com/2020-ldap-channel-binding-and-ldap-signing-requirement-for-windows
SASL-LDAP binds that do not require a signature and Simple LDAP binds over unencrypted connections are prevented.
Elevated log levels and event IDs can be used to detect non-signed LDAP connections.
The increased log can be enabled in the registry on the domain controller. To do this, set "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NTDS\Diagnostics\16 LDAP Interface Events" from 0 to 2 on the domain controller. (After the modification, this setting must be changed back to 0).
With a filter in the Windows Eventlog on the IDs: 2886, 2887, 2888, 2889 (alternatively 2886-2889) the hosts can be determined, which establish SASL-LDAP Binds, which do not require a signature, and Simple LDAP Binds over unencrypted connections. To do this, customize the LDAP server in Aeneis.
Instruction:
-
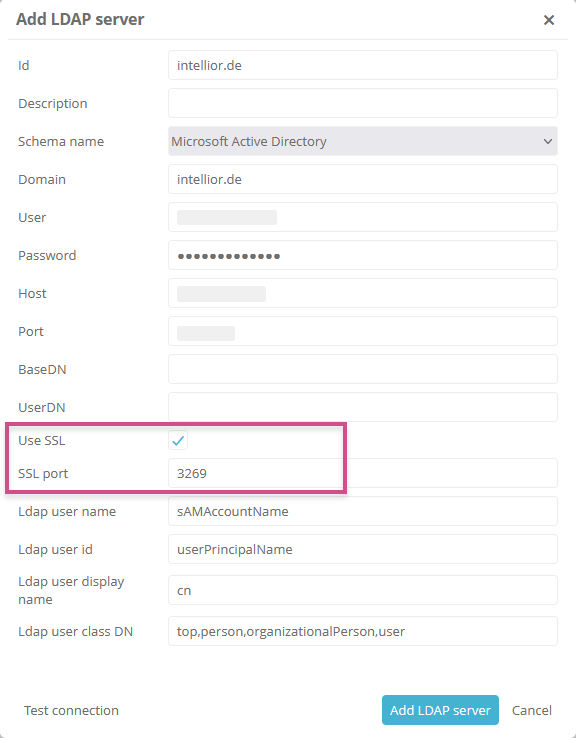
Open the ServerAdministration
-
Under Authentication | LDAP, open the properties of the LDAP server
-
Enable the Use SSL property
-
Enter the SSL port
-
Test the connection
-
Confirm the Import self-signed certificate dialog with Yes
-
Save the properties
Result:
The Aeneis server uses an encrypted LDAP connection. This is possible through the generated aeneis-client-keystore.jks file in the application data directory. In order to continue logging in via LDAP on the FatClient, this file (aeneis-client-keystore.jks) must also be present on the client installations.
-
(For server operation with HTTP) Copy the file to the application data directories of the clients.
-
(For server operation with HTTPS) Remove the secure connection in the clients in the server connection and set it again. Then accept the certificates.